SSH access
SSH, (Secure Shell) access gives you secure remote access to the system shell of your server.
Depending on the complexity of your project, you might or might not use SSH much.
SSH security
As you transition into the world of self-managed NixOS servers with secrets and databases with customer data, you need to prioritize SSH key security.
The most important message on this page is: SECURE YOUR SSH KEYS. And make it mandatory for every system admin of your servers.
Your SSH keys live in your /home/ship/.ssh folder on your server.
Password protect SSH key
A password that you remember, but is hard to crack is vital.
Consider password protecting ALL your SSH keys. Having one passwordless key with access vital services can undermine your secure keys.
Github has a simple guide on working with SSH key passphrases
Pros
- No need to bring anything. Password is stored in your head.
Cons
- Strong password are hard to remember and tedious to write
Hardware key (Yubikey)
You can generate SSH keys directly on a hardware security key like Yubikey, giving you physical SSH keys.
Shipnix will also eventually support WebAuthn hardware key support on the web dashboard.
There are several alternatives if you want to use SSH keys on a hardware key.
- yubikey-agent (currently used by Shipnix creators)
- xeiaso.net: How to Store an SSH Key on a Yubikey (you just need OpenSSH 8.2+)
- NixOS wiki has an article about Yubikey
Pros
- Bring your physical SSH key to any computer
- Enhances security on many services (soon too)
Cons
- The hardware keys costs a bit to purchase, and you might want a spare key
- If you use
yubikey-agent, you must have this installed on every computer where you need to use your keys
Connect to your server
Connecting via SSH to your server is simple as:
ssh ship@youripaddressIf you have a domain set up, you can use this instead of your IP address:
ssh ship@yourdomain.comAdd SSH keys on DigitalOcean
Uploading your SSH keys on DigitalOcean is a time-saver because you can select to add them to the server when you create a new server from .
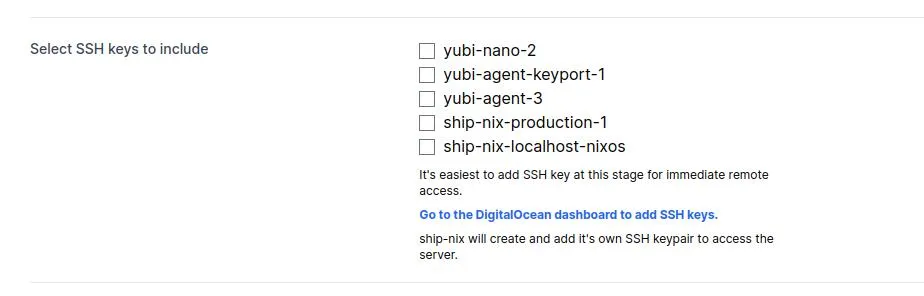
Give and revoke SSH access to server
You can manage who gets to access your server by removing and adding SSH public keys to the /nixos/authorized_hosts file in your project repository.
It’s possible to move authorized_hosts out of version control, but we do not recommend it as this complicates your setup and doing something wrong here can lock you permanently out of your server.
If you want users to access the source code, but not the server, a better way would be to keep NixOS configuration and application separate and only give developer access to the application code.
Troubleshooting
ERROR: publickey denied
If you get an error message saying your public key is denied, it means that the computer your are trying to connect from is not authorized by your NixOS server.
To authorize your computer, you need to locate your public ssh key in your ~/.ssh folder.
cat ~/.ssh/id_rsa.pubThen append the contents of the public key file to your server-config/authorized_keys file in your project.
If you want this computer to access all new servers, you can add your SSH key to your DigitalOcean account. Then, each time you create a new server with ship Nix, you can simply select to include the SSH key automatically.
Read the DigitalOcean docs about how to add SSH keys